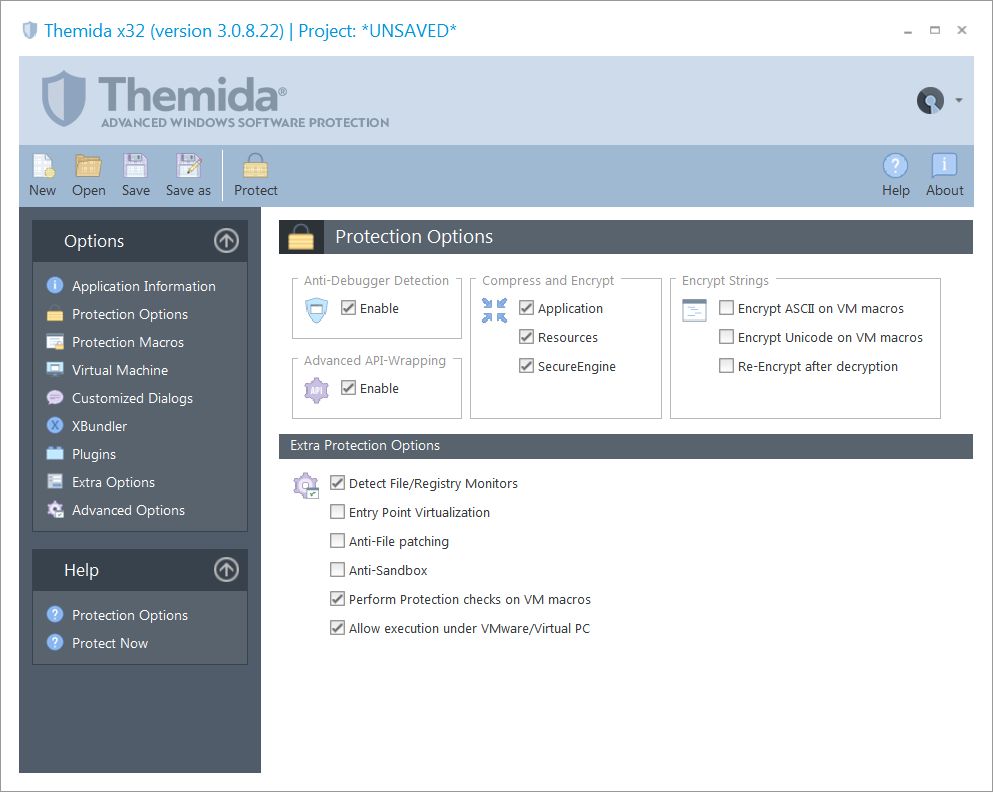
In the Protection Options panel you can select the different protection options that you want to include in your application. By default all the protection options are enabled. If a specific protection option is not needed for your application it can be removed to speed up the execution of your application and make the protection code smaller.
Anti-Debugger Detection
This option will enable anti-debugger detections inside the protected application, detecting when a kernel or software debugger is debugging a protected application.
Advance API-Wrapping
This option will enable advanced API-Wrapping techniques that keep an attacker from identifying the different APIs that are used by a protected application. The API-Wrapping option has a very small penalty in the execution speed in your application in case that your application is calling a specific API massively. In any case, there are internal options that can help you to unselect specific functions from being wrapped. Please, contact us for further information.
Compress and Encrypt
You can select if your application, resources and the protection boot loader will be encrypted and compressed. There is a small penalty in the execution time before your application starts but it's recommended to keep those options enabled for further protection.
Encrypt Strings
When you insert Virtual Machine macros in your source code (or via an external MAP file) you can encrypt all references to strings that appear inside the macro markers (START - END). The string will be removed from the original location and it will be moved inside the protection code area in an encrypted form. Once that the string is going to be referenced by your code, it will be decrypted at that specific point in order to deliver it to the required code.
If you are just using ASCII strings in your application, you should just check the "Encrypt ASCII on VM macros" option. If instead, your application is using Unicode strings, you should just check the "Encrypt Unicode on VM macros" option. You can go to the "Protection Macros" panel and select a specific macro from the list, after that click on the lower panel tabs (Ansi Strings and Unicode Strings) in order to see that strings that are found inside the selected protection macro.
This option is basically the same as putting a STR_ENCRYPT macro inside each Virtual Machine Macro that you have inserted. If you are just interested in protecting specific strings that appears in specific macros that you have inserted, you should not use this option and use instead a STR_ENCRYPT macro inside your Virtual Machine Macro.
The option "Re-Encrypt after decryption" applies to encrypted strings from VM macros and those ones from the STR_ENCRYPT macro. Basically that option encrypts again the string when the VM_END or the STR_ENCRYPT_END marker is executed. Notice that this option might not be compatible with your application, in case that your code is accessing to the string after the STR_ENCRYPT_END marker.
Extra Protection Options
•Detect File/Registry Monitors: This option detects common tools that monitor access to the Windows File and Registry system by a specific application. If your application stores sensitive information in the Windows File or Registry system, you should enable this option.
•Entry Point Obfuscation: This option produces the equivalent result as putting a VM macro in the very first instructions that are executed in your application. This option is not compatible with all applications and you should uncheck it in case that your application does not start when protected.
•Anti-File Patching: This options detects when a modification has been done to the protected application from an external source (like a virus, cracker or any other application). If you are planning to put another compressor on top of your protected application or do some external modifications to the protected file on disk, you should not check this option. If this option is set and and there is a modification in your protected application, SecureEngine will display the Customized Dialog "MSG_ID_FILE_CORRUPTED". You can edit the error message or handle that specific error event from your plugin DLL.
•Anti-Sandbox: This option detects common sandbox applications. A sandbox application virtualizes file and registry access in order to avoid direct/real access to the file/registry system.
•Perform Protection checks on VM macros: When you insert a VM macro (TIGER VM, FISH VM, etc.) inside your application you can perform extra protection checks before the your protection macro is executed. This option checks if your application has been partially attacked by an attacker.
•Allow execution under VMWare/Virtual PC: This option allows your application to be run under common virtual environments like VMWare, Virtual PC, VirtualBox, etc. In case that you want to restrict the execution of your protected application under these virtual environments, you should uncheck this option.